EZOfficeInventory integrates with the SCIM protocol so you can manage the identity data of your employees on the cloud and seamlessly provision them access and user rights into the EZOffficeInventory application from any identity provider including Azure AD.
1.What is SCIM?
SCIM, or System for Cross-domain Identity Management, is an open standard that automates user provisioning for your organization. It communicates user identity data of your employees from identity providers to service providers.
An identity provider (IdP) is a system that contains a robust directory of user identities and single, consistent login credentials for each of your employees. Azure AD is an example. A service provider (SP) is an enterprise SaaS application that requires these user identities so your employees can log into the application.
The SCIM protocol ensures that any changes made to user identities in the IdP, such as Azure AD are automatically synced in the SP i.e. EZOfficeInventory.
2. Why Use SCIM?
Managing user lifecycle is crucial for businesses. As companies grow or experience turnover, their employee count keeps changing. They need a quick and easy way to add or delete user accounts in their company directories and simultaneously authorize or revoke employees’ access to various business applications.
Our integration with SCIM simplifies the user experience by automating your user provisioning processes. It automatically creates users in your EZOfficeInventory account as you create them in IdP tools like Azure AD. Since data is communicated automatically, it saves your IT teams valuable time and reduces the risk of error stemming from manual data entry.
Note: Our SCIM integration currently supports Azure AD and Okta only. Other IdP systems like OneLogin shall be supported soon.
EZOfficeInventory’s SCIM integration with Azure AD offers various benefits. These include:
- Centralized user management: Manage the user identities, access rights and privileges, and action permissions of your employees and teams from a single space.
- Compliance with security policy: Mitigate security risk with consistent login credentials and single-sign-on (SSO) capability as employees no longer need to sign in to each of their accounts individually. This also reduces the need for password resets.
- Ready-to-use integration: Save your IT team the effort of in-house custom development with our ready-to-use integration.
3. SCIM Prerequisites
Before you set up SCIM with Azure AD, you need to consider some pre-requisites. You must have:
- The Tenant URL and Secret Token. See step 4.1.
- Global Administrative rights for the Active Directory.
- Access rights to set up Enterprise applications.
4.[How-to] implement SCIM user provisioning with Azure AD
Let’s walk you through some basic steps on how to implement SCIM-based user provisioning with Azure AD!
Step 1: Enable SCIM in EZOfficeInventory
To enable SCIM in your EZOfficeInventory account, follow the pathway: Settings → Add Ons → User Provisioning via SCIM and select ‘Enabled’. Hit ‘Update’.
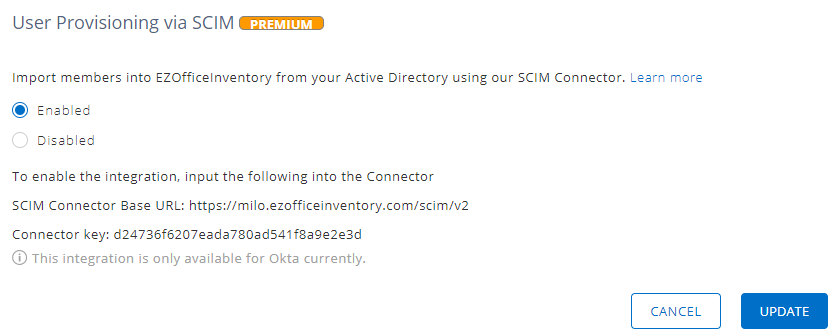
This action reveals additional information shown below.
- SCIM Connector Base URL
- Connector Key
You will need to enter the two values in the ‘Tenant URL’ and ‘Secret Token’ data fields respectively in Step 2.
Step 2: Add EZOfficeInventory in Azure AD
Before you go ahead and start provisioning users, you must first add the EZOfficeInventory application in your Azure portal.
The process is very simple.
1. Go to your Azure Portal and sign in. Note: Make sure you are in the correct directory!
2. Navigate to ‘Azure Active Directory’on the left-hand side.

3. Go to Enterprise Applications → All Applications → New application.
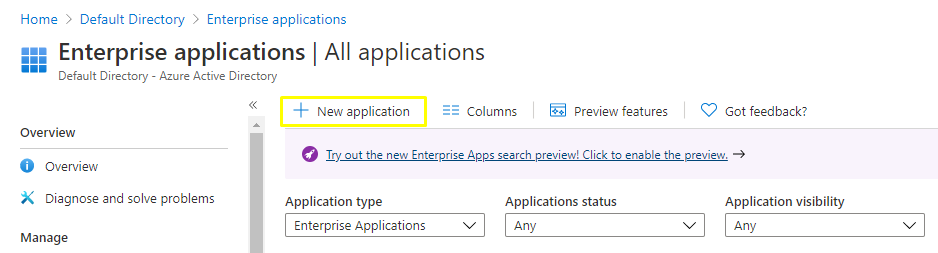
4. Select ‘Non-gallery application’.
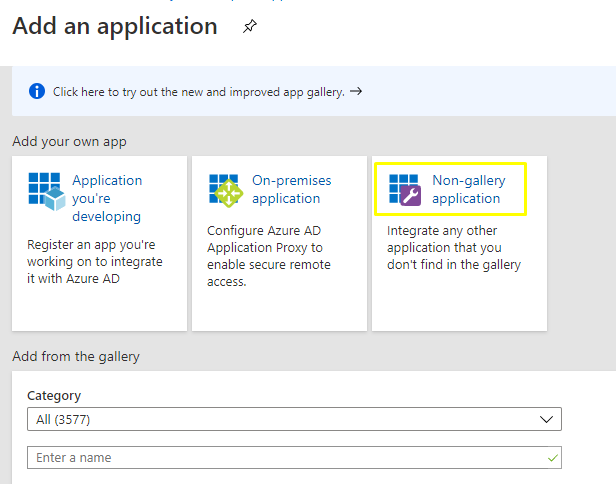
5. Add the name of the application, and click ‘Create’. Please do not choose EZOfficeInventory application appearing as recommendation below. The application currently recommended doesnot support SCIM.
The application has been created in your Azure Active Directory.
Step 3: Configure the SCIM connection in Azure AD
Now, configure some additional settings in your Azure portal.
- Go to the Provisioning tab in the Manage section and click on ‘Get Started’.
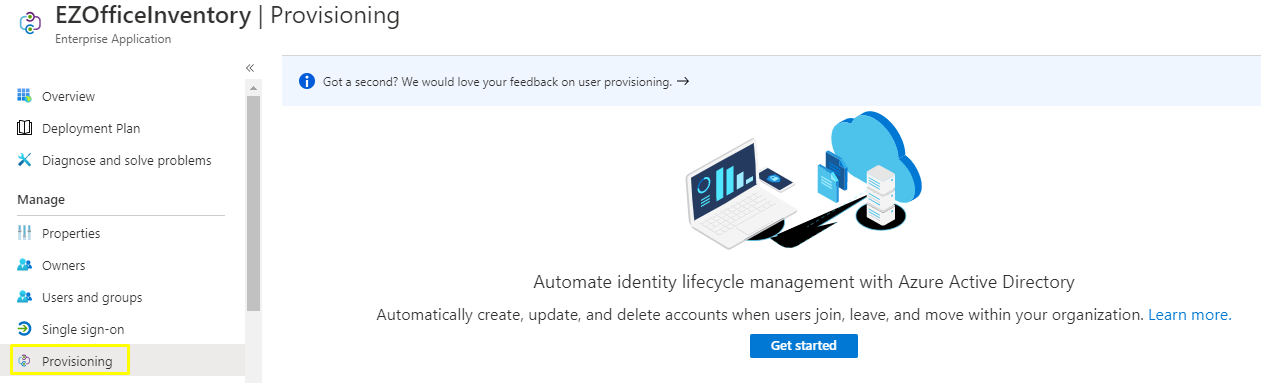
2. Set the Provisioning Mode to ‘Automatic’.
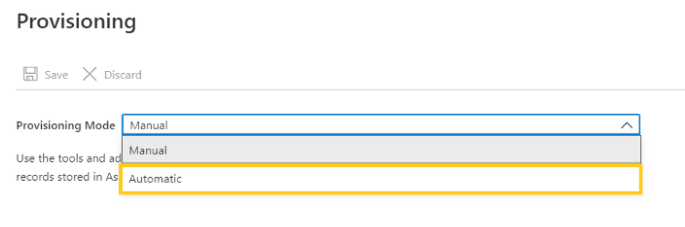
3. Under the Admin Credentials section, input the SCIM Base Connector URL and the Connector Key (from Step 1) into the Tenant URL and Secret Token fields respectively. Click ‘Test Connection’ to ensure Azure AD can connect to EZOfficeInventory.
If the connection fails, ensure your EZOfficeInventory account has Admin permissions and try again.
4. In the Notification Email field, enter the email address of the person or group who should receive the provisioning error notifications and check the checkbox ‘Send an email notification when a failure occurs’.
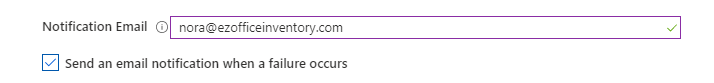
5. Click ‘Save’.
Once the provision settings have been saved, you’ll get the following notification.
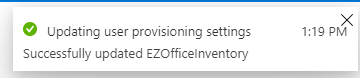
5. Provisioning User(s)
To enable the Azure AD provisioning service for EZOfficeInventory, carry out the steps outlined below:
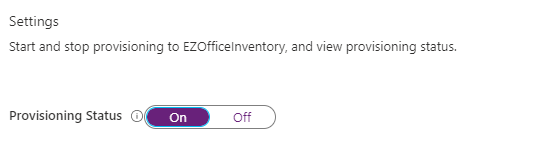
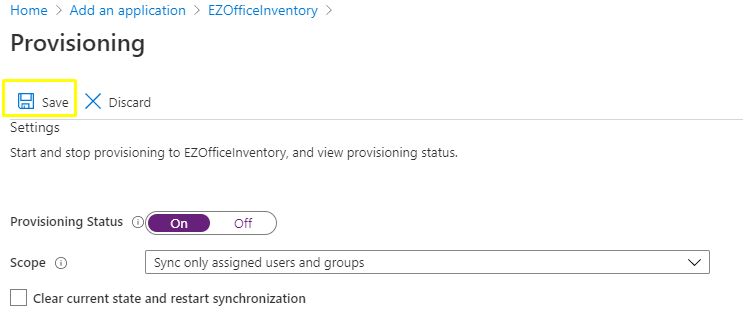
- Go to the Settings section and change the Provisioning Status to ‘On’.
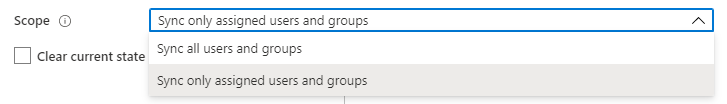
2. Define the users and/or groups that you would like to provision to EZOfficeInventory by choosing the desired values in Scope in the Settings section.
3. As you can only provision users and not groups for Azure AD via SCIM, disable the “Provision Azure Active Directory Groups” from Mappings.
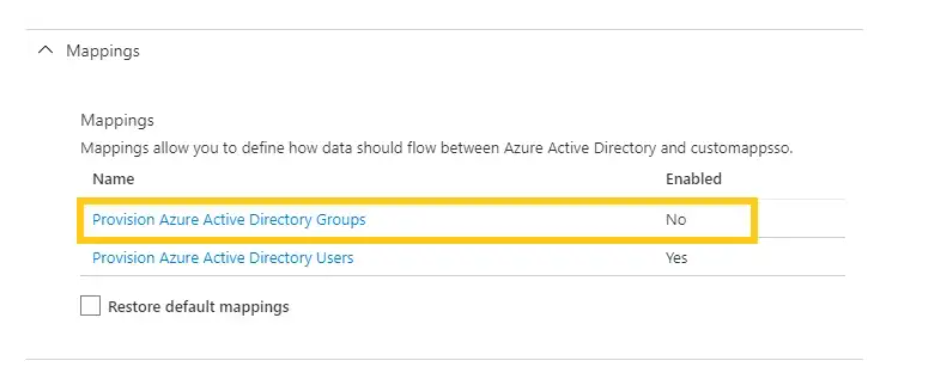
Note: We don’t support group provisioning in EZOfficeInventory. However we support group assignment in Azure; which acts as if users were manually assigned in EZOfficeInventory. Learn more about scope of group assignment.
4. When you are ready to provision, click ‘Save’.
5. If you selected ‘Sync only assigned users and groups’, please navigate back to the Users and Groups section of the EZOfficeInventory App. Click on ‘Add user’ to add relevant users and/or groups.
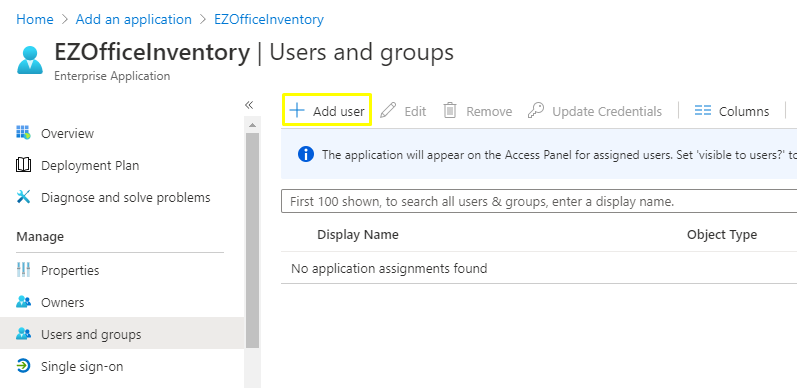
6. Click on the relevant User’s details and hit ‘Select’.

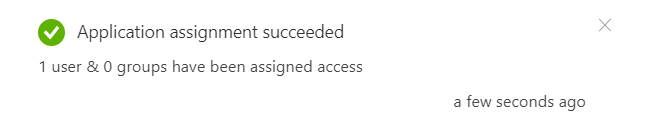
7. Click on ‘Assign’.

You’ll get the following alert once the assignment has been successful.
8. Now, go to the Provisioning section in the EZOfficeInventory application and click on ‘Refresh’.
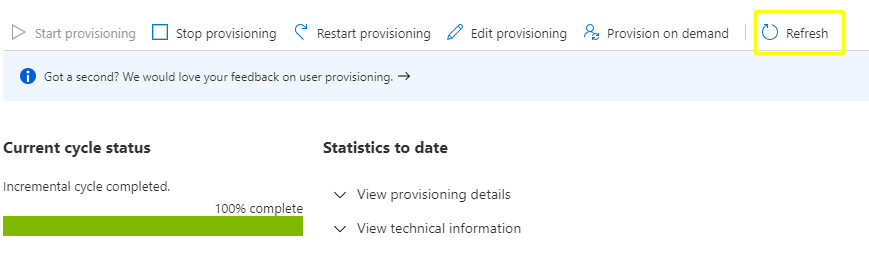
This shall sync the selected User in your EZOfficeInventory account and provide them access rights into the application, as shown.
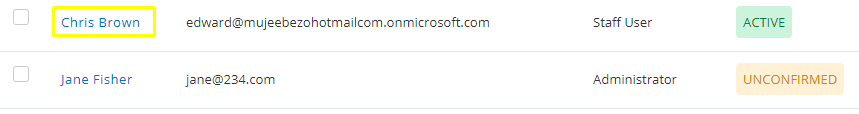
Deprovisioning users: When a user is deleted/deprovisioned in Azure AD, they will be deactivated in EZOfficeInventory given that the user is not linked to any asset in EZOfficeInventory. In case a user cannot be deactivated in EZOfficeInventory they will not be deactivated in Azure. In this case, an error message will be sent back on AZURE. Learn more about deprovisioning here.
In case a user is deleted in EZOfficeInventory, the user will be bought back in the next sync with SCIM. In order to permanently deactivate the user in EZOfficeInventory, delete the user in Azure AD and in the next cycle the user will be inactive in EZOfficeInventory.
Read more: How to Implement User Provisioning via SCIM with EZOfficeInventory and Okta
6. Import Users Into Custom Roles
To import users into Custom Roles, there are two steps:
6.1. Custom Role provisioning in Azure AD
Custom Roles for users can be set via the SCIM attribute mapping feature in EZOfficeInventory (custom roles can be set via scim provisioning alongwith other attributes).
For that, first we need to select the Azure AD user profile attribute that needs to be mapped to a Custom Role in EZOfficeInventory via SCIM. Open a user profile and select the attribute you want to be mapped to Custom Roles.
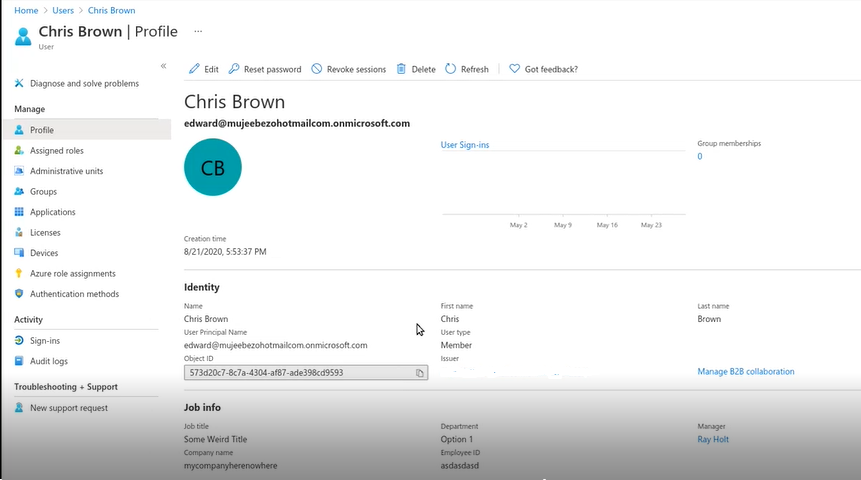
Note: The Custom Role is mapped in EZOfficeInventory via the name of the role so there should be a field in user profile that has the values same as the role that you want users to be provisioned to.
Let’s say the Custom Role is listed under ‘Department’.
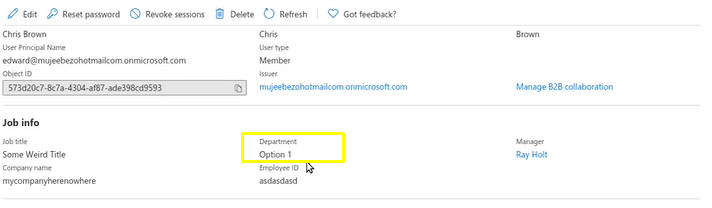
This is the user attribute we want to map into EZOfficeInventory through user provisioning in Azure AD.
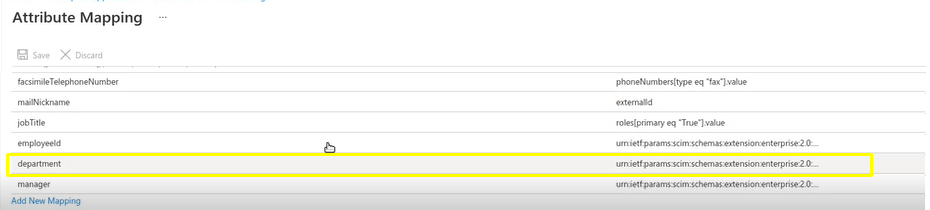
Go to Attribute Mapping and find the user attribute with the Custom Role in the user profile. Copy the SCIM attribute on the right side, this will be used to map Custom Roles in EZOfficeInventory in Step 6.2. In this example the user attribute with Custom Role is Department.
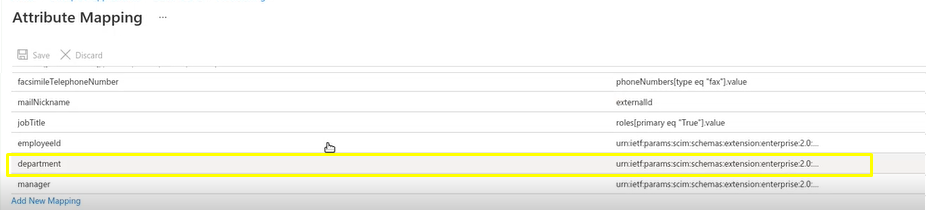
You can even provision a Custom Role to a default value if there is no field for your user profiles holding a Custom Role. In order to do that, select a field in the user profile that has a blank value.
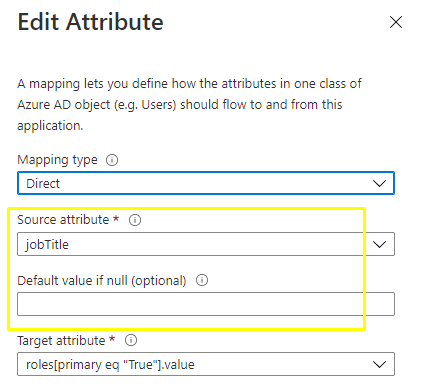
Go to the attribute mapping table and click on the blank user attribute you want to set as a default value for Custom Roles. An overlay will appear where you can enter the default Custom Role.
Now the Default value you enter here will be set as a Custom Role.
6.2.Custom Role provisioning in EZOfficeInventory
Go to Settings → User Provisioning via SCIM.
Here you can map different member attributes including Custom Roles via SCIM in EZOfficeInventory. To provision Custom Roles from Azure, select the ‘Import Users to Custom Roles’ button.
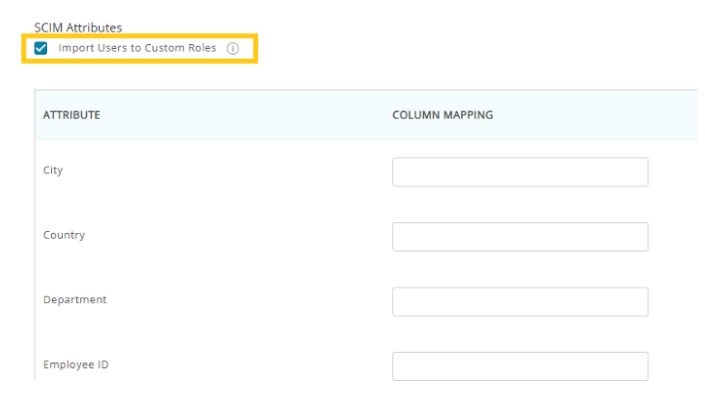
Once you have selected the setting, the following options would be visible on the attribute and column mapping table:
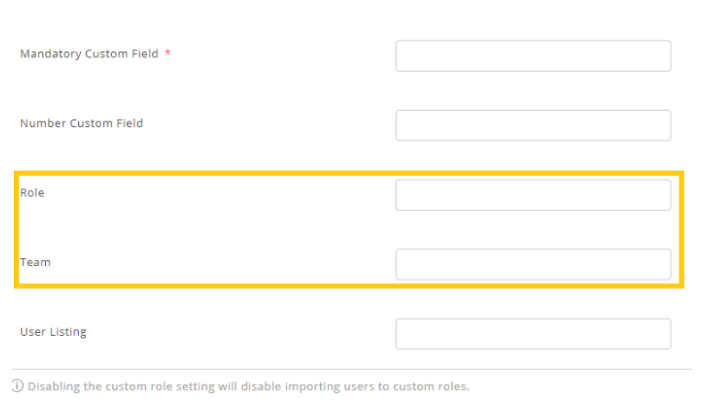
Now, the SCIM attribute you copied in Step 6.1 has to be entered in Roles in EZOfficeInventory.
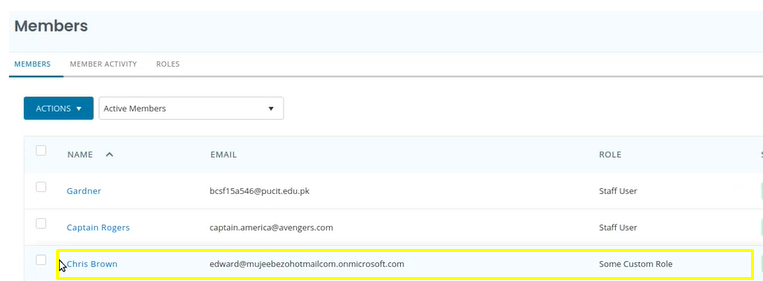
Once you enter the attribute click Update. When updated, you will be able to view the Custom Role in Members for the user. After this setting, whenever a new member is created or updated via SCIM, the Custom Role will be automatically assigned.
Note: Automatic provisioning takes a while, however you can manually provision users to update attributes in EZOfficeInventory.
7. Mapping of active directory attributes
As an Administrator, you should be able to view, edit and add which user attributes must flow between Azure AD and EZOfficeInventory whenever user accounts are provisioned or updated.
Attribute mapping can be helpful when you have to map important aspects like street address, employee badge number, or location etc.
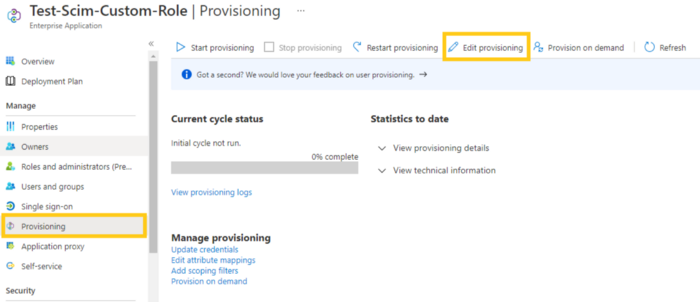
For mapping Active Directory Attributes to EZOfficeInventory, log in to your Azure AD portal and click on ‘Enterprise Applications’. Choose the relevant SCIM application and an overview page will pop up.
On the App Overview page, select the ‘Provisioning’ option. Then, click on ‘Edit Provisioning’ as shown below:
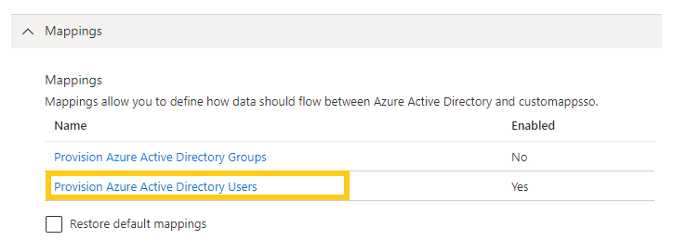
Next, click on the ‘Mappings’ configuration and a dropdown will appear. From here, select ‘Provision Azure Active Directory Users’.
This redirects you to the Attribute Mapping page. The usernames are exhibited under Azure Active Directory Attribute while the values under customappsso Attribute are mapped in EZOfficeInventory.
For instance, as shown below, userPrincipalName from Azure AD will be mapped against userName in EZOfficeInventory as we have directed.
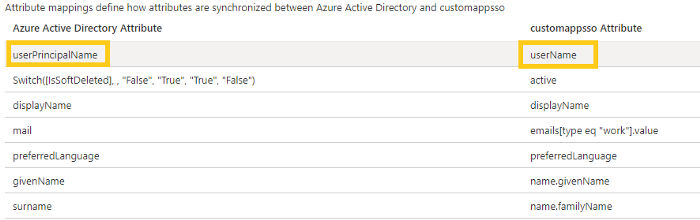
This way, if you want to map Azure Active Directory Attributes onto the EZOfficeInventory application, you can simply copy and paste the specific attribute name from customappsso Attributes.
7.1 Adding custom attributes
If you want to add more attributes, then follow the steps given below:
- Scroll down to the end of the Attribute Mapping page and select ‘Show advanced options’.
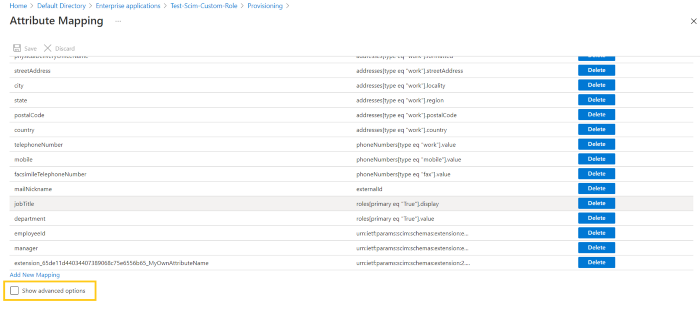
2. After this, click on the ‘Edit attribute list for customappsso’ button.
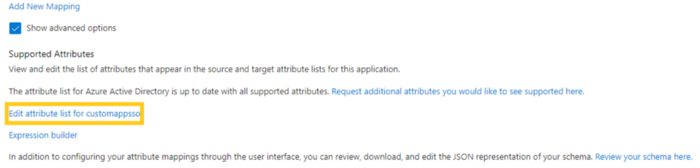
3. A new attribute can be added with the help of a command prompt. After extracting commands from the command prompt, you get the option to add a custom attribute as illustrated below:

4. Add a custom extension attribute. However, ensure that you keep the format precisely the same as it is in Azure documentation. For example, the following format should remain the same:
urn:ietf:params:scim:schemas:extension:2.0:CustomExtension:
You can add the attribute name at the end.
This will enable users to add custom attributes to Azure AD. Once this process is complete, you can easily map that attribute from Azure AD to a field in EZOfficeInventory. Copy the entire name (as highlighted below) and paste it in the SCIM Attributes section of EZOfficeInventory settings as shown below:
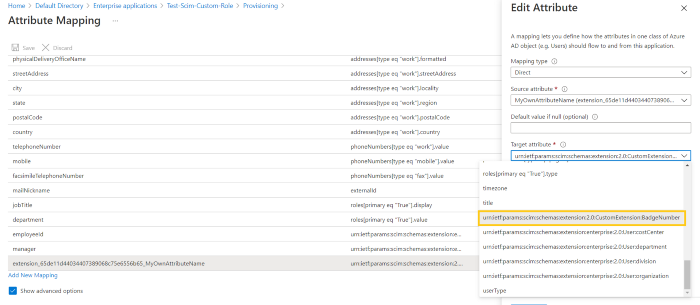
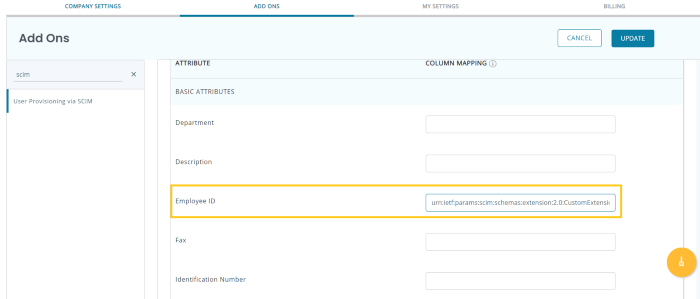
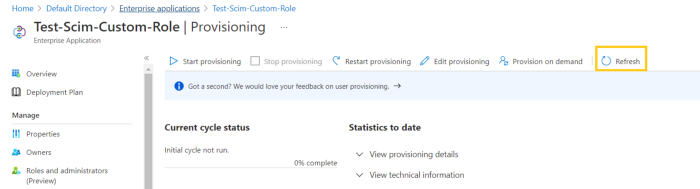
Click ‘Update’ to refresh settings. Once done, go back to Azure Active Directory → Enterprise Applications → Application Name and click on ‘Refresh’.
Troubleshooting
The role created in AD is provisioned to a staff user in EZOfficeInventory. Why could this be happening?
There are a couple of reasons for incorrect syncing of roles via SCIM. Either the role is not correctly mapped or the role does not exist. In such cases the role will be mapped according to the following setting:
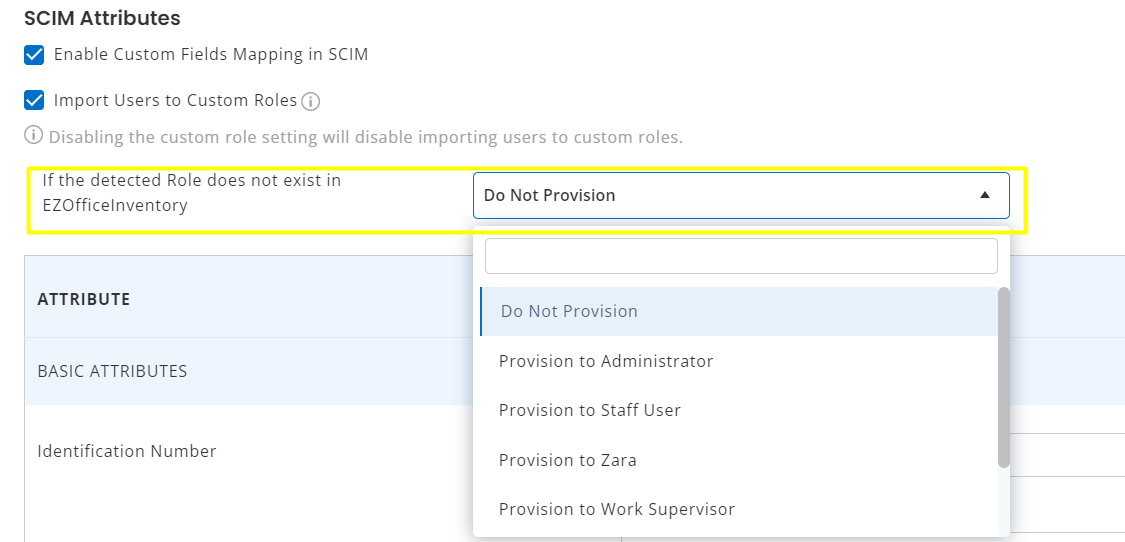
In case the role is not detected in EZOfficeInventory, the role will be mapped according to the one selected in the setting above. To avoid incorrect provisioning you can also select “Do Not Provision”. This will simply send an error message in AD that the role does not exist in EZOfficeInventory.
About EZOfficeInventory
EZOfficeInventory is the leading asset tracking software. It allows you to track, maintain, and report on equipment from anywhere, at any time. We offer a free 15-day trial – no credit card required!







